This article is about HTTP Strict Transport Security (HSTS) and has covered the most precise and relevant content related to it.
Topics Covered –
- What is HSTS?
- What is HSTS preload list?
Page Contents
What is HSTS ?

HTTP Strict Transport Security (HSTS) is a new HTTPS header which a website must send in response to the client’s request in order to force HTTPS on the website.
My Story
This is something I encountered while I was learning Laravel. So there I was on youtube looking for the best tutorial on Laravel and Traversy Media is what I found, and I would say that this is one of the best channels to learn the programming language you want.
So, When I was initially setting up the environment, there came a point when Brad Traversy (founder of Traversy Media) and creator of this tutorial, created a virtual host for the application to load, and he used a virtual host as lsapp.dev.
And since I was following the tutorial step by step I too created the same virtual host on my local machine and when I was trying to load the application, the chrome browser was showing me this.
![What is HSTS? - HTTP Strict Transport Security HTTP Strict Transport Security (HSTS) forces HTTPS on [dot]dev extension](http://rohutech.com/wp-content/uploads/2020/03/HTTP-Strict-Transport-Security-HSTS-forces-on-dotdev-extension.png)
As you can see when I was trying to run the application in the browser, the application could not run. Whereas in his tutorial the application was running just fine (not sure how his application was running as this policy was introduced in November 2012, whereas his video he published it around June 2017).
But anyway, I was trying to make it run on my browser but all my efforts were gone in vain. I tried updating my virtual host entry to some other domain name. I even added some more apache directives to the entry but still no luck.
Then, when I started googling about .dev extension, to see why my domain with .dev extension is not loading the application in the browser, that’s where I encountered about HSTS web service policy.
Wikipedia Definition –
HTTP Strict Transport Security (HSTS) is a web security policy mechanism that helps to protect websites against protocol downgrade attacks and cookie hijacking. It allows web servers to declare that web browsers (or other complying user agents) should interact with it using only HTTPS connections, which provide Transport Layer Security (TLS/SSL), unlike the insecure HTTP used alone. HSTS is an IETF standards track protocol and is specified in RFC 6797.
source : wikipedia
Rohutech Definition
Basically, HSTS is a policy which forces a web browser to always load a domain using HTTPS protocol instead of HTTP. HSTS does this by checking the domain list in HSTS preload list.
Layman’s terms
If you try to access a Bank website you will just type in the bank’s name say ‘abc.com’ without adding HTTPS or HTTP. The first request always goes via HTTP that is with no encryption, this is where the hacker (man in the middle) takes advantage and tries to listen to your request (this happens if your ISP is compromised or you are on an unsecured network connection like a public or open WIFI) and in response presents you a dummy website which looks very similar to the original website you know of. So when you try to use your credentials on the dummy website hacker gets all the information and can use it for his good.
But if that bank website has implemented an HSTS response header then it forces a web browser to load it only on HTTPS protocol. But again this will happen when the client receives its first response because the client’s browser will come to know that this website has to be accessed only on HTTPS only when it reads/receives HSTS response header from the website.
Unfortunately, the first time that you access the website, you are not protected by HSTS. If the website adds an HSTS header to an HTTP connection, that header is ignored. This is because an attacker can remove or add headers during a man-in-the-middle attack. The HSTS header cannot be trusted unless it is delivered via HTTPS.
This is where the HSTS PRELOAD LIST comes into the picture.
What is HSTS preload list?
HSTS preload list contains a set of domains that are to be accessed only via HTTPS protocol.
The reason why https is being forced on lsapp.dev is that domains ending in .dev are now in the HSTS preload list, which means they can only be accessed over HTTPS with a trusted certificate. Other major browsers also implement HSTS using the same preload list, and most likely will soon pick up the .dev entry.
The recommended TLD for local testing environments is ‘.test’ which is reserved for that use case, and won’t have this issue.
Preload HSTS
A domain or website owner can submit their domain to hstspreload.org, in order to get their domain name listed in the HSTS preload list. This will result in their domain being hard-coded as HTTPS-only in Chrome’s list. And, Since all major modern browsers also have preload lists based on Chrome’s list, this allows domains to be protected against man-in-the-middle attacks for a huge amount of users.
But before submitting your domain to hstspreload.org, there are few prerequisites that your website must fulfill.
In order to be accepted to the HSTS preload list through this form, your site must satisfy the following set of requirements:
- Serve a valid certificate.
- Redirect from HTTP to HTTPS on the same host, if you are listening on port 80.
- Serve all subdomains over HTTPS.
- In particular, you must support HTTPS for the
wwwsubdomain if a DNS record for that subdomain exists.
- In particular, you must support HTTPS for the
- Serve an HSTS header on the base domain for HTTPS requests:
- The
max-agemust be at least31536000seconds (1 year). - The
includeSubDomainsthe directive must be specified. - The
preloaddirective must be specified. - If you are serving an additional redirect from your HTTPS site, that redirect must still have the HSTS header (rather than the page it redirects to).
- The
For more details on HSTS, please see RFC 6797. Here is an example of a valid HSTS header:
Enable HSTS on your website
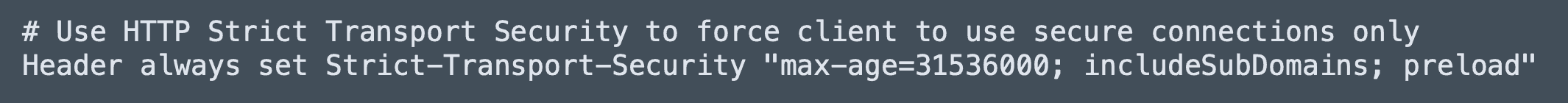
Copy the following to your applications .htaccess file.
# Use HTTP Strict Transport Security to force the client to use secure connections only
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"Once the header is set, you can verify it by looking at the response header in developer tools
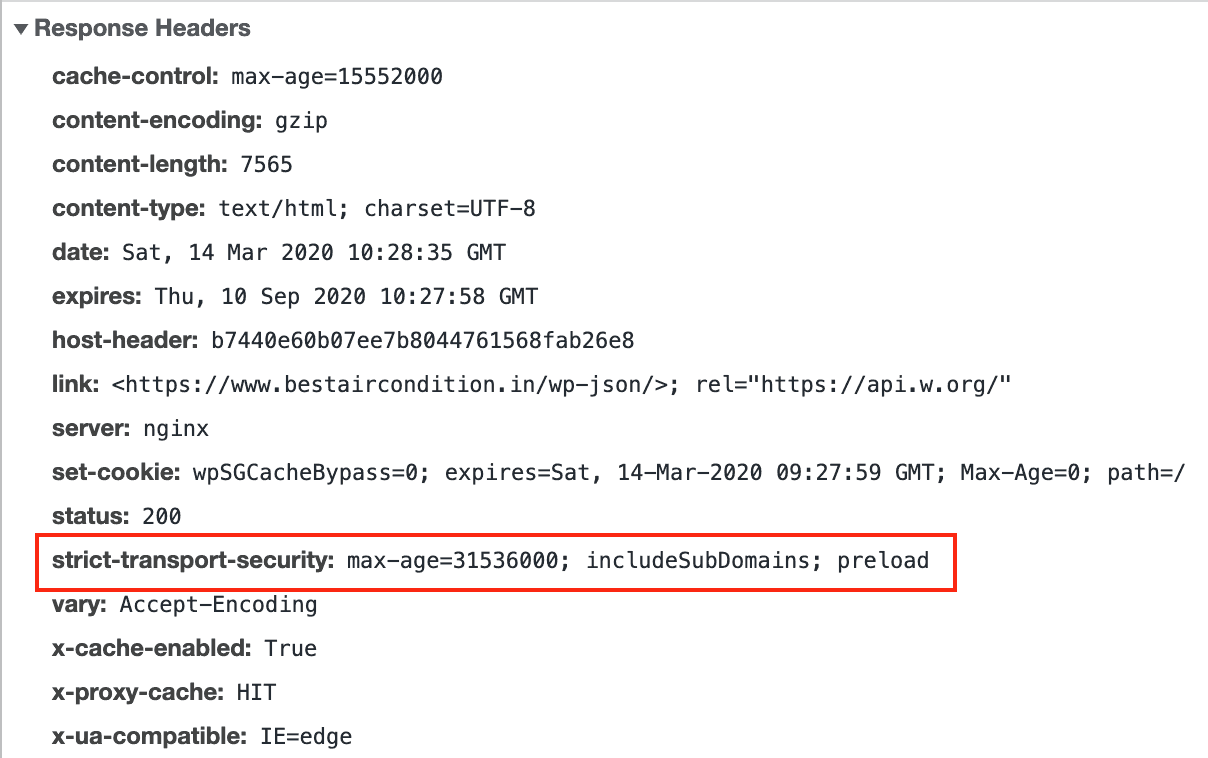
Some more good articles on HTTP Strict Transport Security (HSTS)
- HSTS – How to Use HTTP Strict Transport Security
- Firefox 4: HTTP Strict Transport Security (force HTTPS)
I hope this article gave you some insights on HTTP Strict Transport Security (HSTS), if you like this article let me know in the comments, Also subscribe to my YouTube channel to get more information on similar topics.











